0 Introduction
0.1 Motivation
With the emergence of advanced sensor, control, and Internet of Things technologies, smart energy grids are gradually replacing the traditional power system [1-2].However, the application of new information technology has resulted in the exposure of the operating environment of smart energy grid.In particular, smart energy grid, a typical energy cyber-physical system (e -CPS ), is encountering new cyber-physical security risks [3-4].These potential security risks have caused immeasurable impact on people’s lives [5].For instance, an unknown cyberattack occurred in Russia and Iran in 2018, affecting 200,000 routers worldwide.Further, the power grid attack of European energy giant Energias de Portugal (EDP) resulted in the leakage of considerable amount of confidential information in 2020.To address emerging security risks caused by cyber-physical attacks in smart energy grids, the United States has formulated all types of energy countermeasures.First, an energy security research report was presented by United States Department of Energy [6].Subsequently,North American Energy Reliability Corporation conducted a investigated cyberattacks in smart energy grids [7].As discussed above, the construction of smart energy grids faces enormous cyber-physical security challenges.
As shown in Fig.1, smart energy grids have achieved efficient operation of power systems, such as diesel,wind, and solar energy power generation, transmission and distribution, and power consumption.However, the intelligence and openness of cyber-physical network interactions render smart energy grids vulnerable to various cyber-physical attacks.Supervisory control and data acquisition (SCADA) requires energy scheduling to maximize the utilization of new energy sources such as wind and solar energy.Under these conditions, data in the network transmission can easily be attacked by hackers.Liu et al., designed novel cyber-physical attacks, using which,the detector employed χ2 detection to facilitate avoidance of detection thresholds[8].Notably, attackers can evade the χ2-based bad data detection in energy management system by designing a bank of false data.Therefore, Amini et al.proposed dynamic load alteration attacks (DLAAs) aimed at changing the generator load frequency [9].By slowly injecting false data into the load information, an attacker can destabilize the entire power network.Therefore, this study aimed to develop a novel cyber-physical collaborative detection framework for DLAAs in smart energy grids.
0.2 Background
To date, many studies have focused on ensuring the security of smart energy grids.Existing attack detection methods can be divided into two categories: cyberlayer ( style="vertical-align: middle; text-align: center;">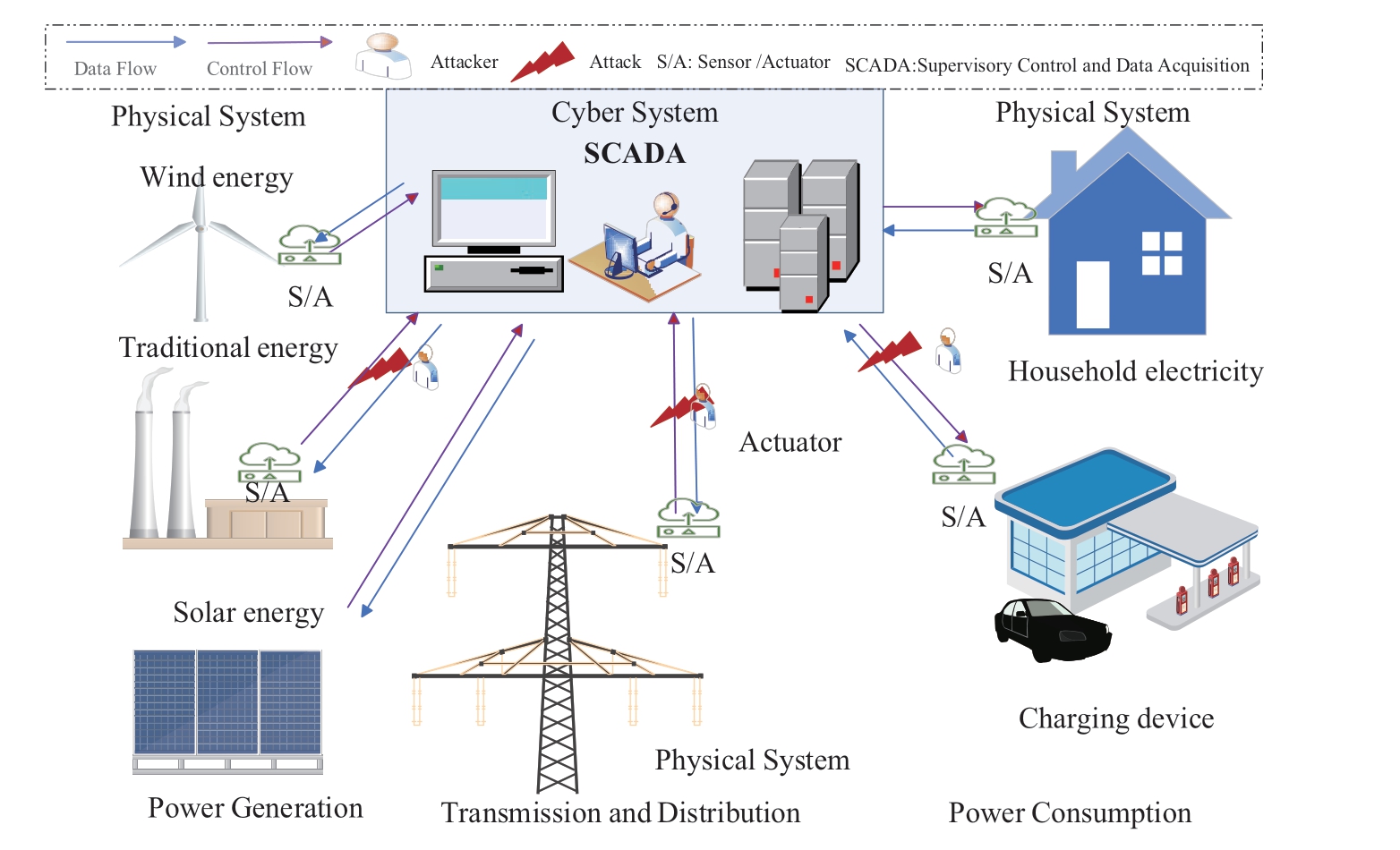
Fig.1 Cyber-physical system-smart energy grids
In contrast to the aforementioned cyber-layer-based detection methods, physical-layer (model)-based detection methods have been highly motivated by researchers.Physical layer (model)-based detection methods rely on model residuals to determine state anomalies in a power system.In [15], an adaptive fading Kalman filter-based detection method for DLAAs was developed for a power system.Considering vulnerable loads, a robust sliding-mode observer-based reconstruction and detection method for DLAAs was proposed [16].Further, a detection and location method against bias load injection attacks was proposed for smart grids [17].In addition, an on-time sliding-mode observer-based attack detector was constructed to improve the attack detection time and detection accuracy [18].In [19],the detection and isolation of false data injection attacks in smart grids was a scheme proposed to tackle false data injection attacks based on the designed nonlinear interval observer.Compared to style="font-size: 1em; text-align: justify; text-indent: 2em; line-height: 1.8em; margin: 0.5em 0em;">· Advantages of above existing works:
style="font-size: 1em; text-align: justify; text-indent: 2em; line-height: 1.8em; margin: 0.5em 0em;">· Disadvantages of above existing works:
The effectiveness of id="generateCatalog_5" style="text-align: left; text-indent: 0em; font-size: 1.2em; color: rgb(195, 101, 0); font-weight: bold; margin: 0.7em 0em;">0.3 Contribution
To bridge the gap between cyber-layer-based and physical-layer-based detection methods, this study developed a novel cyber-physical collaborative detection and localization framework for DLAAs in smart energy grids.As shown in Fig.2, the proposed collaborative framework includes attack prediction in a cyber system, and attack detection and localization in a physical system.First,a style="vertical-align: middle; text-align: center;">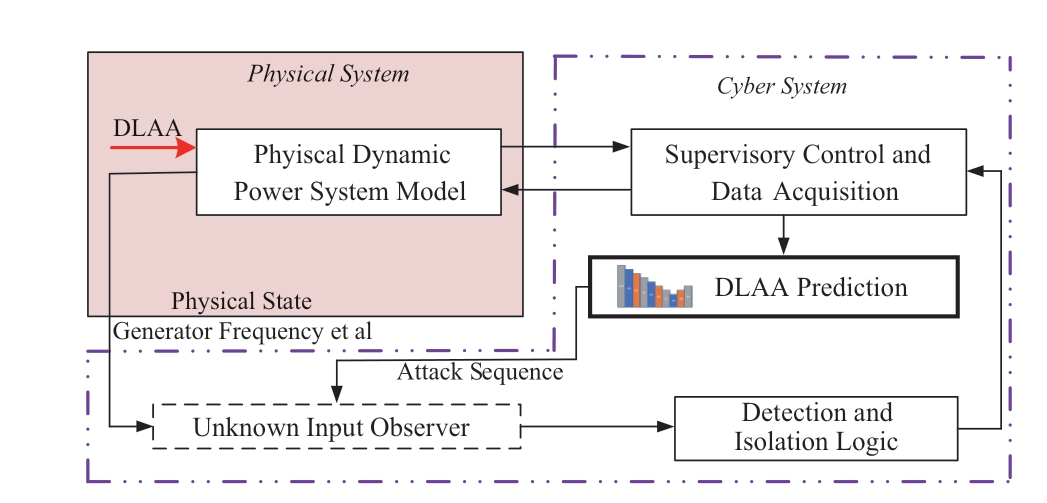
Fig.2 Cyber-physical collaborative detection and localization framework
· A novel cyber-physical collaborative detection and localization framework. The proposed collaborative framework includes attack prediction in cyber systems and attack detection and localization in physical systems,bridging the gap between cyber- and physical-layer-based detection methods.
· A data-driven-based attack prediction method in cyber layer. A dual RBF network was designed to predict the DLAAs in the cyber layer.Consequently, the influence of disturbances on attack prediction were eliminated.Compared with existing methods, the attack prediction performance of the proposed method was improved.
· An unknown input observer-based detection and localization method in physical layer. Based on the established physical dynamic power model, a bank of unknown input observers was constructed wherein the influence of model uncertainty and disturbance were eliminated.Furthermore, an adaptive detection threshold was designed to replace the precomputed detection threshold by considering external disturbances and model uncertainty.
1 Covert Characteristics of DLAAs
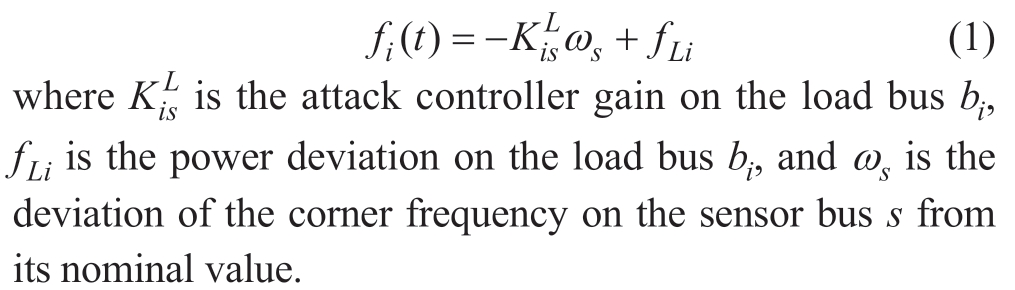
A balance exists between power generation and consumption to ensure the stable operation of smart energy grids.Therefore, attackers aim to destroy this balance,causing blackouts and reactions in transformer relays.By injecting a bank of false data into the cyber network, an attacker can adapt to the generators, creating an imbalance that destroys the generator.Different from the traditional cyberattacks, a covert false data injection attack called DLAA is designed to fool the common detection method based on χ2 detector.According to [20], the attack sequence of the DLAA can be designed as in Eq.(1).
Example 1.Considering the IEEE-14 bus power system(shown in Fig.3) as an example, it was assumed that an attacker can inject a DLAA into bus 6 of the 2nd generator.The attack sequence above was taken from [20].The corresponding change in the running state under the DLAA was obtained, as shown in Fig.4.
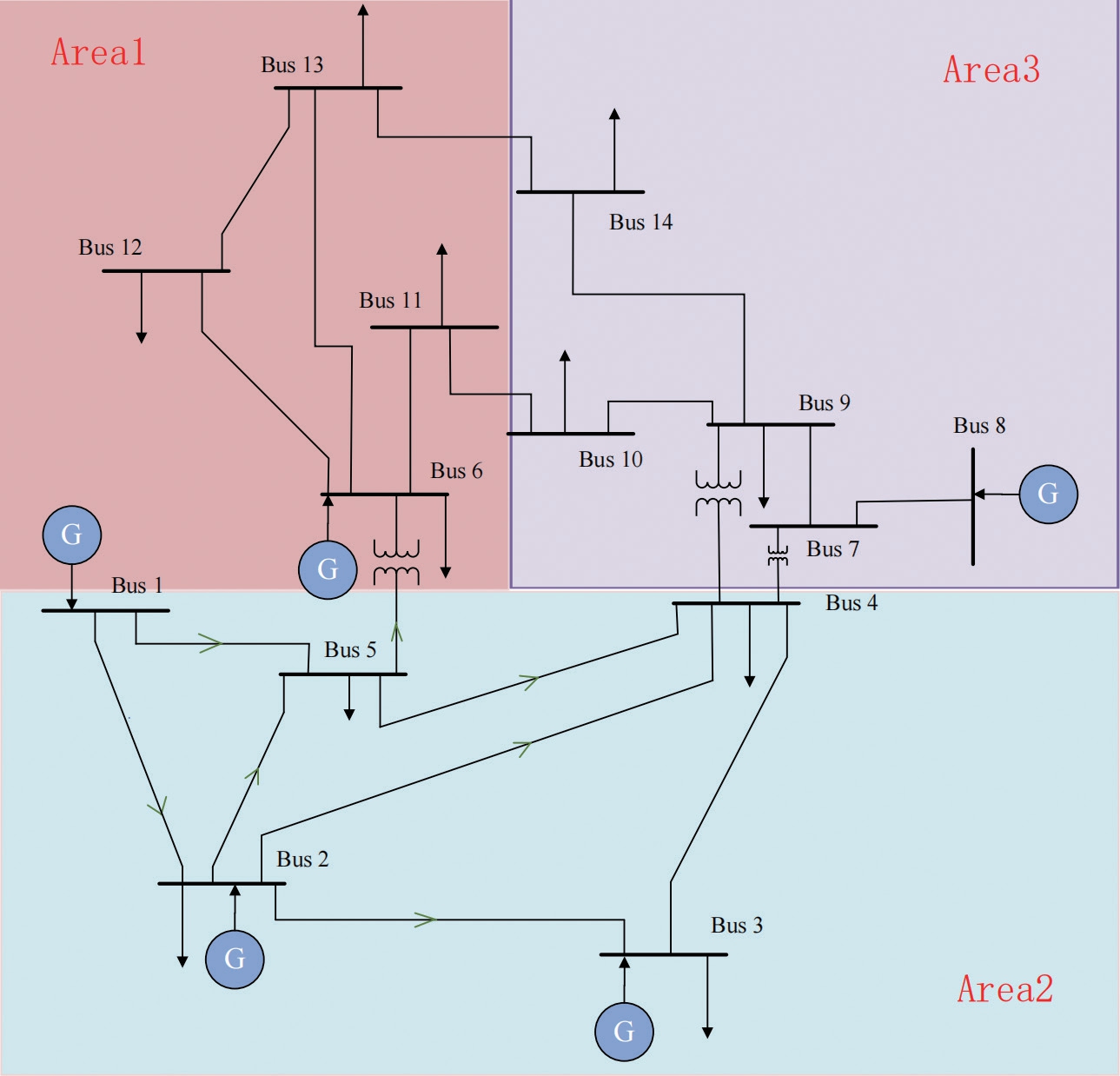
Fig.3 IEEE-14 power system structure topology
As shown in Fig.4, the hacker can tamper with the running state of the generator by injecting a bank of false data, and attackers can cause the working motor to lose load with a continuous deviation of the motor frequency over time.Therefore, this study aimed to develop a novel cyber-physical collaborative detection and localization framework to ensure the stable operation of smart energy grids.
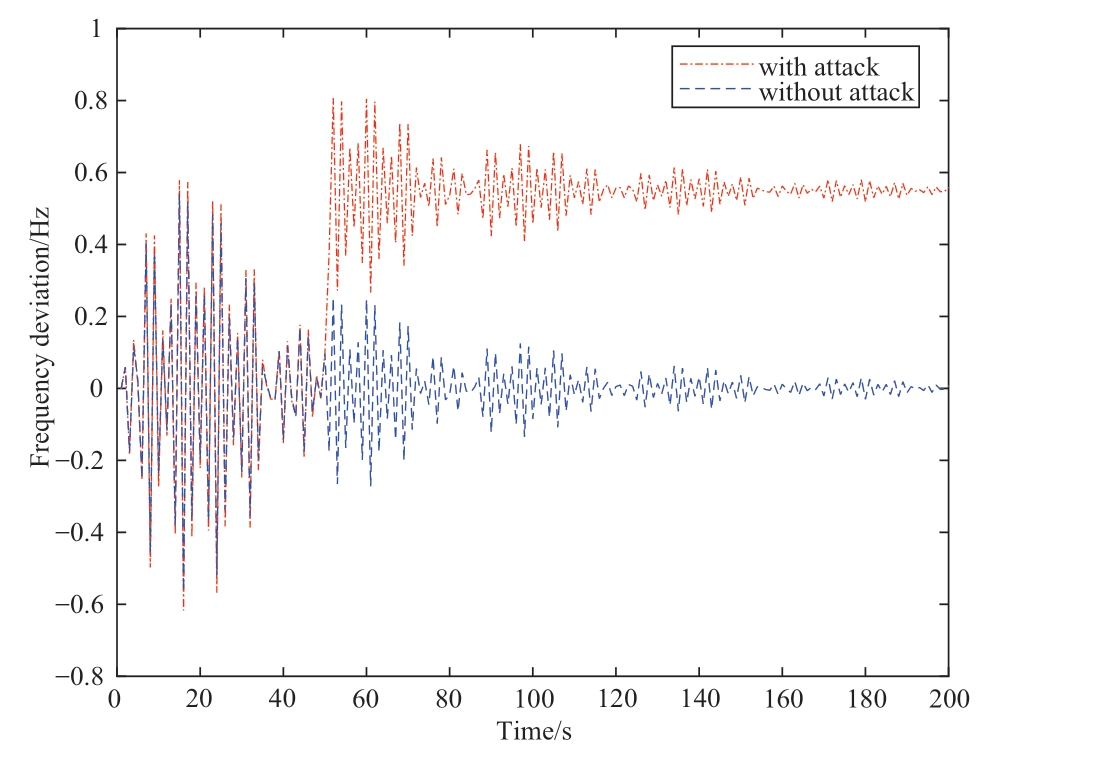
Fig.4 Change of running state under DLAA
2 Cyber-physical Collaborative Detection and Localization Framework against DLAAs
In this section, a cyber-physical collaborative detection and localization framework for DLAAs is presented.Using artificial intelligence methods, a dual-network model was constructed to predict the attack sequence based on the data collected in the cyber layer.Considering the influence of the attack sequence, an unknown input-observer-based detection and localization method was proposed.In the following subsection, the processes of the collaborative detection and localization framework for DLAAs are presented.
2.1 Dual network model-based attack prediction
In this subsection, a dual-layer RBF neural network is constructed to handle the sensor data collected in a cyber system.Considering that the collected data included external interference factors (external disturbances), the proposed RBF neural network comprised two layers.As shown in Fig.5, the first layer of the RBF neural network addressed the influence of external disturbances.Accordingly, the second layer of the RBF neural network was used to predict the attack sequence.
2.1.1 Interference pre-processing
In practice, the collected sensor data include external disturbances, attack sequences, and normal data.Thus,an attacker can design a bank of false data through which detection mechanisms can be fooled.Therefore, the goal of the constructed first layer was to shield the external disturbance, where the expected objective function is designed as
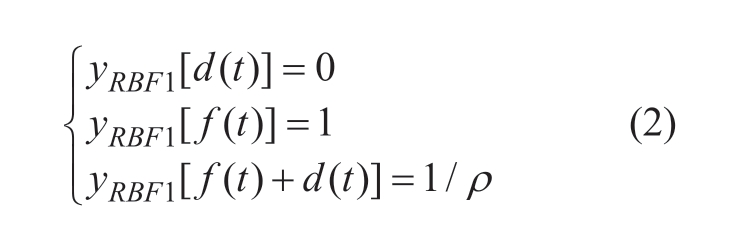
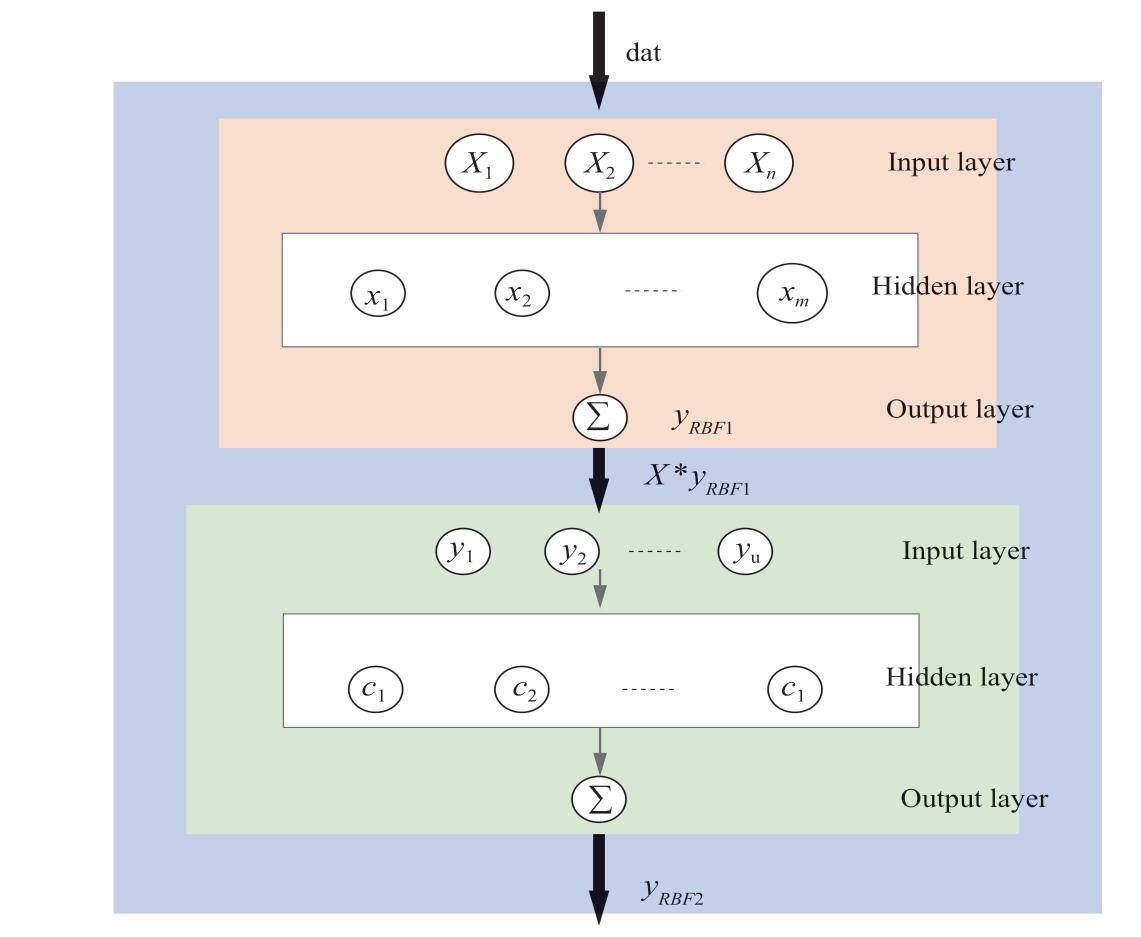
Fig.5 Topology diagram of the dual RBF neural network structure
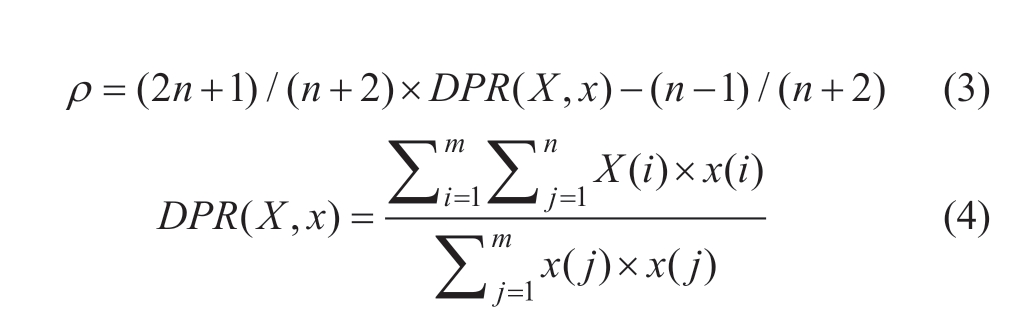
where d(t) and f(t) denote the external disturbance and attack sequence, respectively, yRBF1[]· denotes the expected objective function of the first layer of the RBF neural network, ρ is the similarity coefficient, DPR ( X ,x ) denotes the similarity value, yRBF1 denotes the output of the first layer of the dual RBF neural network, n is the total number of datasets, and m is the number of first hidden layers in the RBF neural network.
Remark 1.In this study, three data input combinations were considered: external disturbance, attack sequence,and disturbance including attack sequence.The maximum output of the objective function is the attack sequence obtained through the design of the first layer of the RBF neural network.
To eliminate external disturbances and predict attacks more accurately, the activation function in the first hidden layer of the RBF neural network is designed as shown in Eq.(5).

Using Eq.(6), the derivative is obtained as
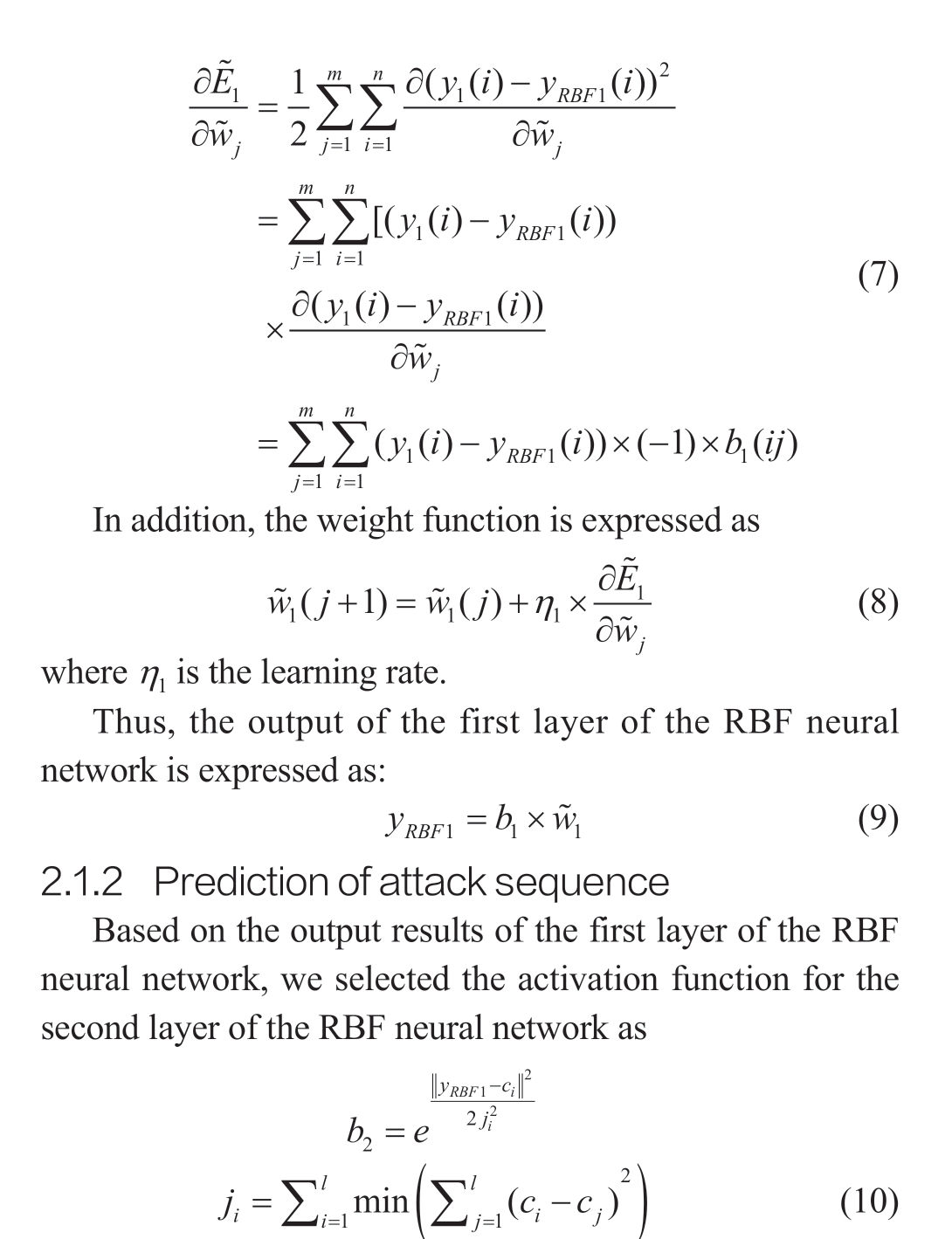
where ci is the center of the second hidden layer Gaussian basis function, j is the field basis width of the second hidden layer node in the RBF neural network, and l is the number of neurons in the second hidden layer.
Remark 2.Here, Eq.(10) indicates that the value of ci represents the sensitivity of the Gaussian basis function to the central data, where ji affects the speed at which the measurement data decrease in the RBF neural networks.Therefore, we introduced the k-means algorithm to optimize the selection of the above parameters.
Similarly, the evaluation function for the second layer of the RBF neural network was chosen as:

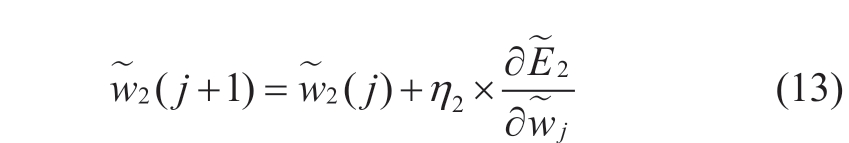
where η2 is the learning rate.
Therefore, the output of the second layer of the RBF neural network is expressed as:
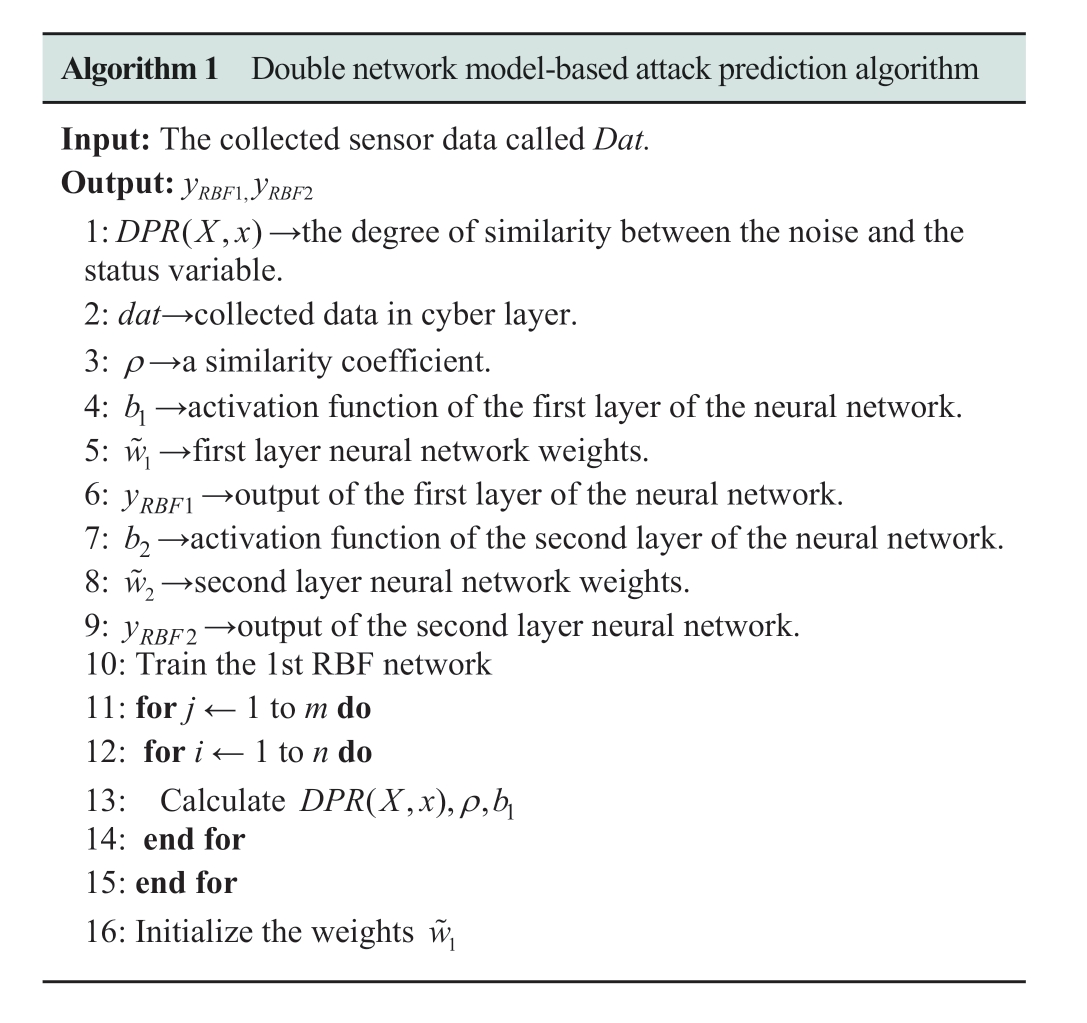
The dual-network model-based attack prediction process can be summarized as follows.Through the design of RBF neural network, such as the expected objective function and similarity coefficient, the influence of external disturbances can be eliminated to the maximum possible extent.The prediction performance of the attack sequence can be enhanced by introducing the k-means algorithm to optimize the selection of parameters.Finally, the pseudocode for the proposed attack prediction process is presented in Algorithm 1.
2.1.3 Evaluation metric
Based on the work in [21], the macro F1-score metric was used to evaluate the accuracy of attack prediction.The macro F1-score indicates the average of precision Pr and recall Re, which can be described as follows:
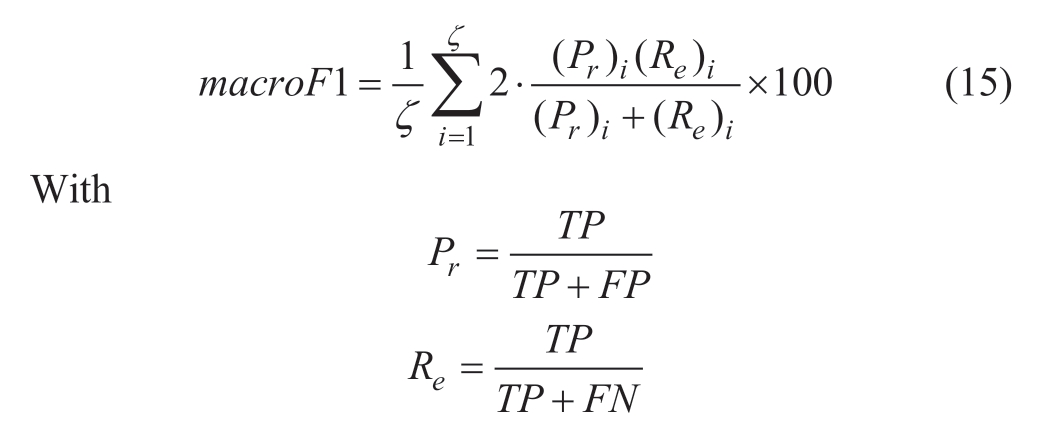
where TP, FP, and FN denote the number of the true positives, false positives and false negatives, respectively,and ζ is the number of data.

2.2 Unknown Input Observer-based Detection and Localization Method against DLAAs
In this subsection, an unknown input-observer-based detection and localization method is developed.Considering the attack prediction results for the cyber layer, a dynamic physical grid model was constructed.Through the design of the observer parameters, the proposed unknown input observer can handle the influence of external disturbances,such as noise and model uncertainty.Subsequently, an unknown input-observer-based detection and localization algorithm for DLAAs was proposed.
2.2.1 Physical dynamic grid model
Typically, attackers aim to change the physical running state of a generator or generator load by injecting DLAAs.Accordingly, a dynamic physical grid model was constructed considering the generator angle and speed.According to [22], the corresponding physical dynamic power swing equation of the generator bus can be described as follows:
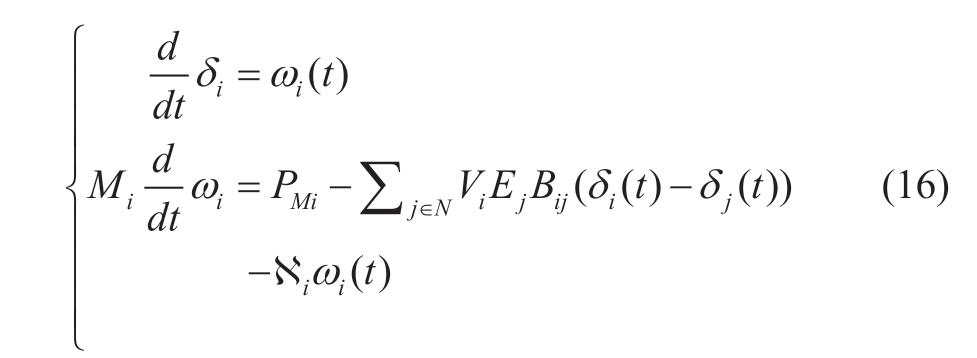
where δi and ωi denote the i generator angle and speed,respectively, Vi and Ej denote the voltages of the generator and load buses, respectively, Mi and ℵi denote the inertia and damping constants, respectively, Bij denotes the susceptance, PMi is the mechanical power input, and N is the total number of buses.
Using Eq.(15), the physical dynamic grid model can be rewritten as follows:
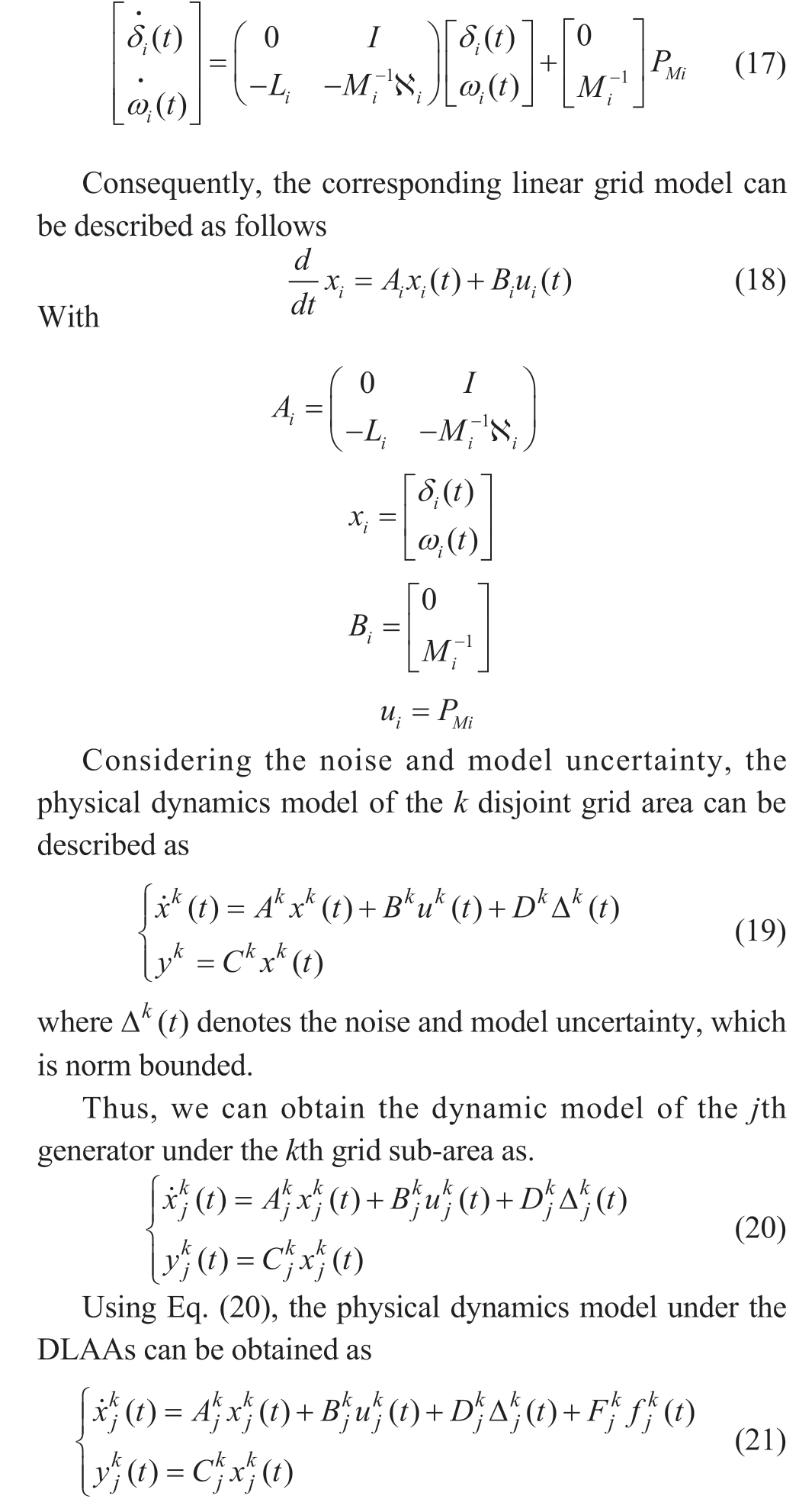
where F is the attack selection matrix and f is the DLAA attack vector.
2.2.2 Design of the proposed unknown input observer
Based on the constructed physical dynamic grid model in Eq.(21), the proposed unknown input observer was designed as follows:
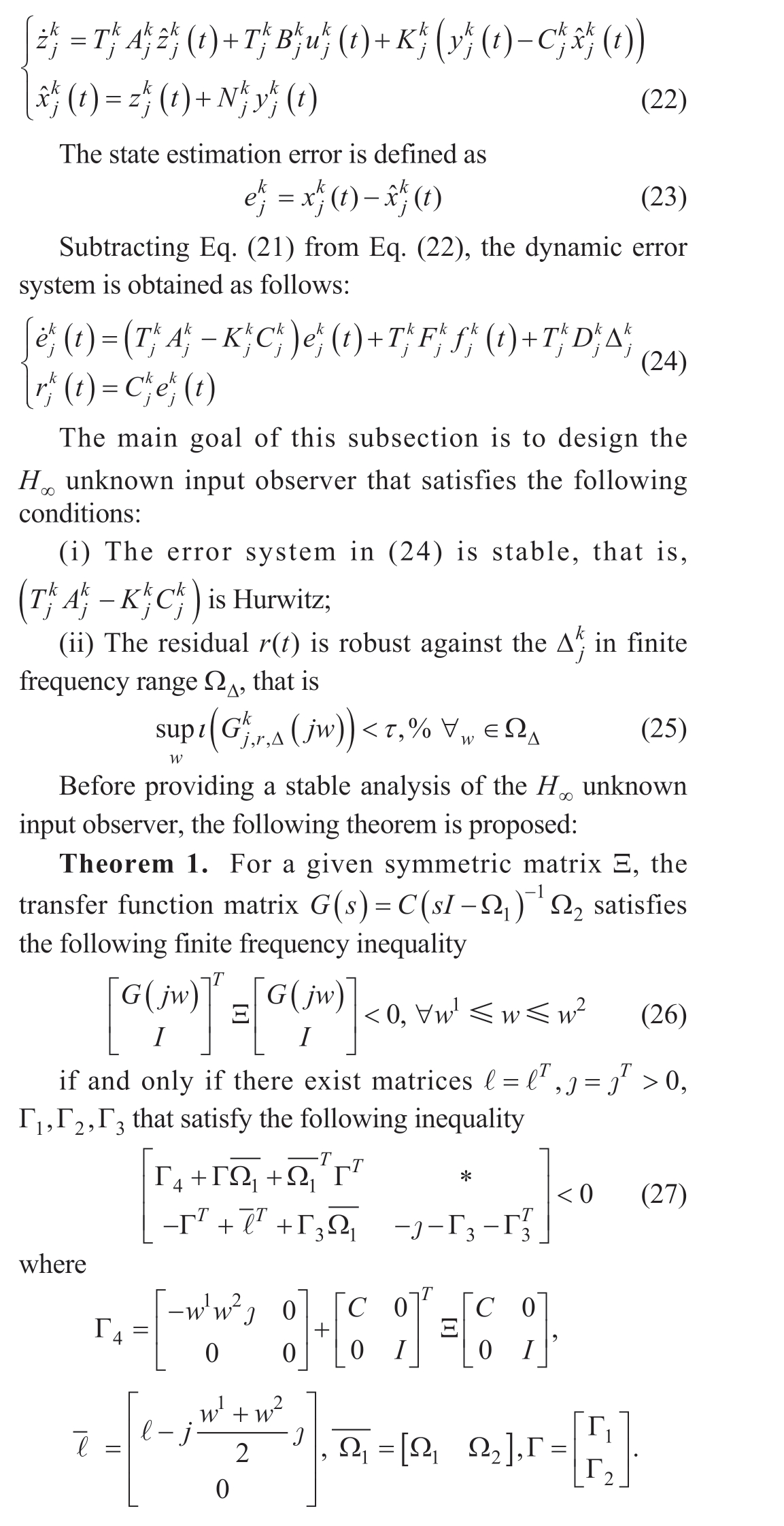
Proof 1.Using the proposed Kalman-Yakubovich-Popov lemma [23], Eq.(26) can be rewritten as follows:


Remark 3.Notably, Theorem 2 provides the design of the H∞ unknown input observer using the method in the finite frequency domain.The designed unknown input observer can estimate the running state more accurately by handling the influence of external disturbances and model uncertainty.
2.2.3 Unknown input observer-based attack detection and localization
Considering the limitations of the precomputed thresholds on detection performance, this study proposed the design of an adaptive detection threshold based on external disturbances and model uncertainty.
Using Eq.(34), the state residuals under the DLAAs can be obtained as follows:

By using Lemma 1, we set the adaptive thresholds as

Based on the above attack detection and localization logic, the detailed processes are summarized as follows.
Step 1: Using the proposed double network model, the attack prediction results in the cyber layer can be obtained.
Step 2: A physical dynamic grid model is established by constructing a bank of proposed unknown input observers.
Step 3: Considering external disturbance and model uncertainty, the adaptive detection threshold in Eq.(44) can be decomposed into:
Step 4: According to the prediction results above for the DLAAs, the established area attack logic in Eq.(45) can be applied.
Step 5: For the attacked area, the injected DLAAs are detected and located based on the proposed node attack logic in Eq.(46).
The injected DLAAs can be detected and located based on the aforementioned cyber-physical collaborative steps.The pseudocode for the above algorithm is summarized in Algorithm 2.
3 Simulation analysis
In this Section, simulations of the IEEE 14-bus and 118-bus grid systems are presented to demonstrate the performance of the proposed cyber-physical collaborative detection and localization framework against DLAAs.Using the regional division method in [26], the IEEE 14-bus (Fig.3) and 118-bus grid systems (Fig.6) comprised three grid areas and five grid areas, respectively.In addition, the learning rates for attack prediction were set as η 1= η2=0.01.
In the following subsections, two cases are presented to demonstrate the performance of the proposed scheme against DLAAs.Case 1 considers the collaborative detection and localization of a single DLAA on a small grid system (IEEE 14-bus grid system), and Case 2 considers the collaborative detection and localization of multiple DLAAs on a large grid system (IEEE 118-bus grid system).
3.1 Case 1: collaborative detection and localization of single DLAA on IEEE 14-bus grid system
It was assumed that hackers can attack the 2nd generator in the 1st area by tampering with the transmission data in the cyber layer at t =100 s.The injected attack sequence can be predicted using Algorithm 1, as shown in Fig.7.To show the prediction performance of the constructed dualnetwork model, evaluation parameters, such as the training performance of the first- and second-layer RBF neural networks, were selected, as shown in Fig.8.The dual-RBF network model-based prediction performance against DLAAs is shown in Figs.9 and 10.As shown in Fig.7,an injected DLAA was present in the grid system.In other words, the injected attack sequence in the cyber layer can be predicted using the proposed attack prediction Algorithm 1.The simulation results in Figs.8(a) and 8(b) demonstrated the excellent training performance of the proposed dualnetwork model.The training errors of the first- and second-layer RBF neural networks were 5.622 u10-6 and 1.269 u10-5, respectively.As shown in Fig.9(a), the accuracy rate of the attack prediction reached 97.86 with increase in the amount of data.Meanwhile, Fig.9(b) shows the receiver operating characteristic (ROC) curve against the DLAA.Evidently, the area of the ROC was close to 1, which describes the attack recognition ability.Thus,the injected attack sequence can be predicted accurately.Compared with existing prediction methods such as Random Forest (RF), Extreme Gradient Boosting (XGB), Logistic Regression (LR), and k-near neighbor (KNN) algorithms,Fig.10 shows the superior prediction performance of the proposed algorithm for DLAA in terms of training time and F-score.It is evident that the proposed dual-network modelbased attack prediction algorithm 1 had the shortest training time (4.72) and the highest F-score (99.93).In summary,the proposed attack prediction algorithm can reduce training time by introducing a two-layer training model structure.In addition, the attack prediction performance was improved by designing a new activation function.
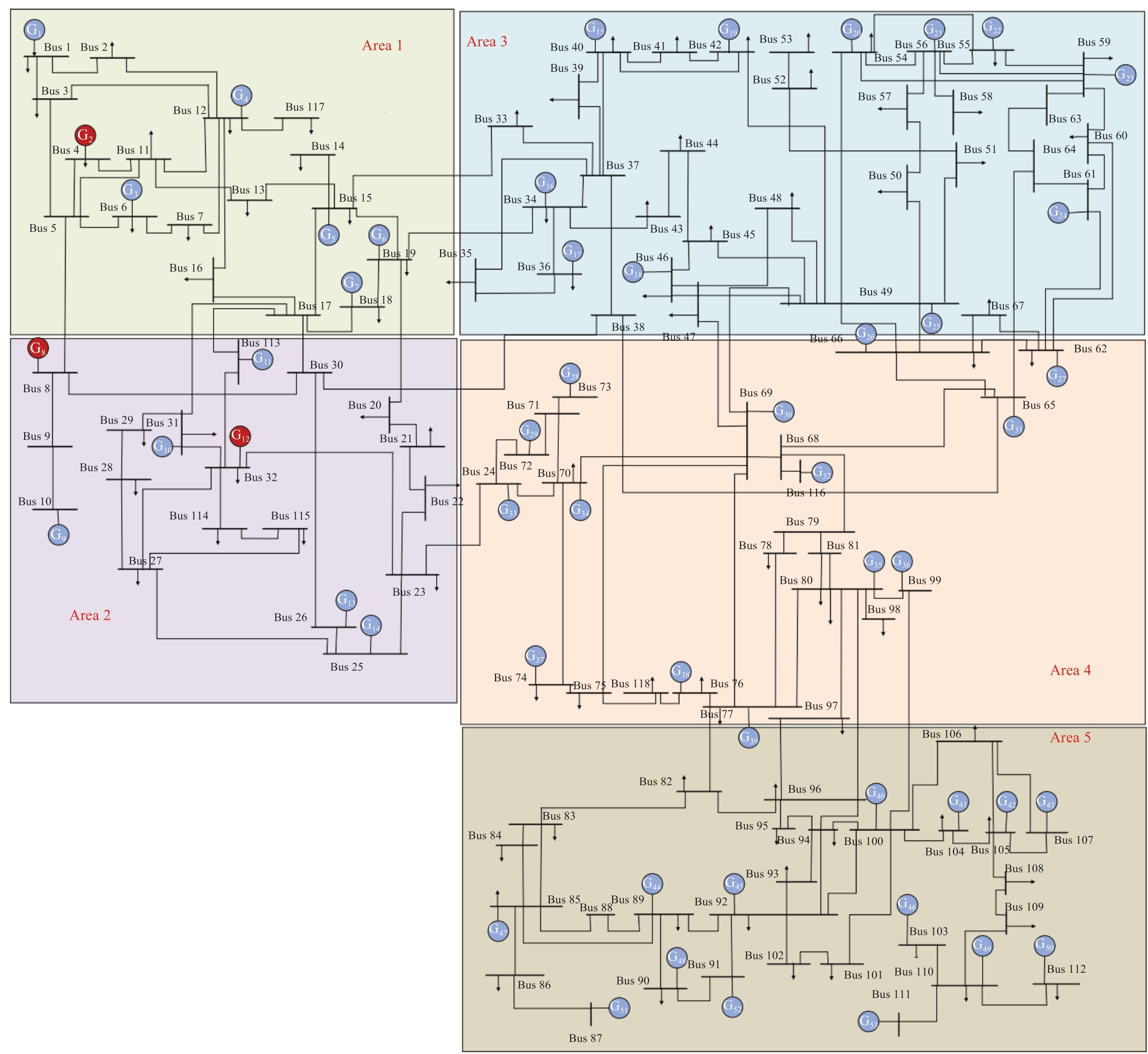
Fig.6 IEEE 118-bus power system structure topology
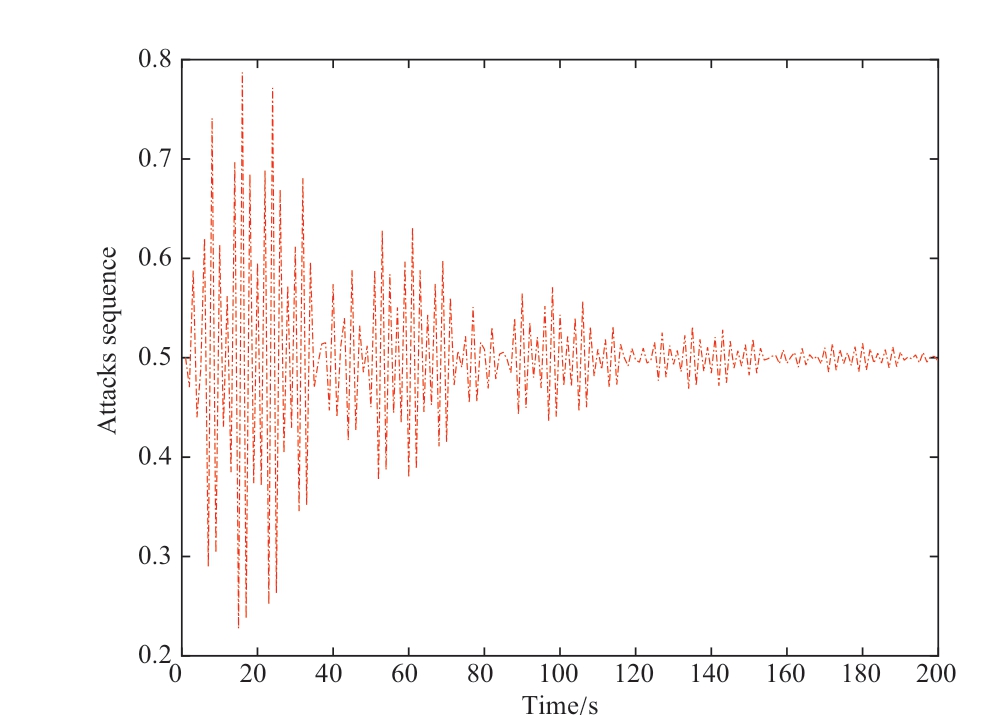
Fig.7 Prediction result of attack sequence on IEEE 14-bus grid system
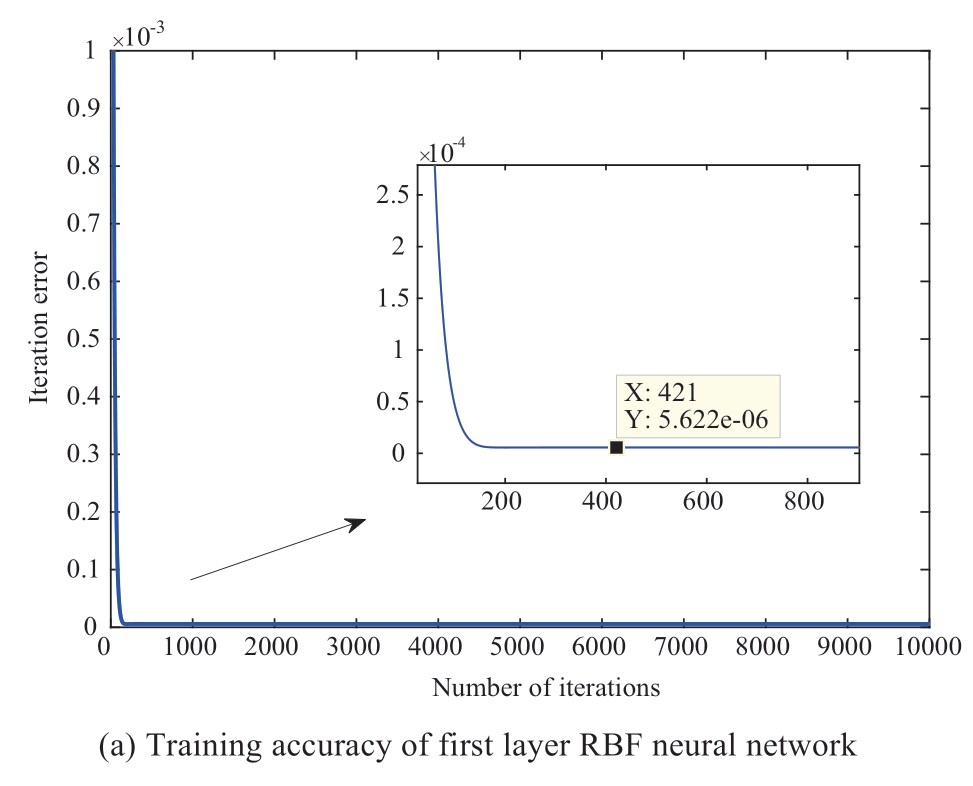
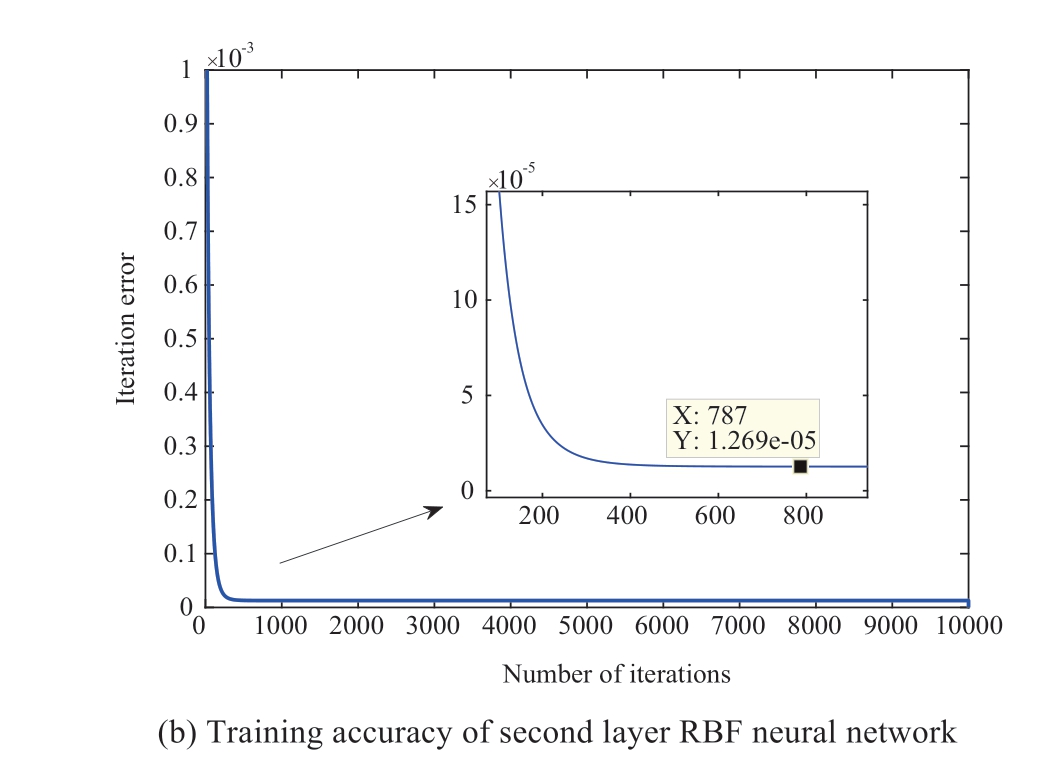
Fig.8 Training accuracy of dual RBF network model
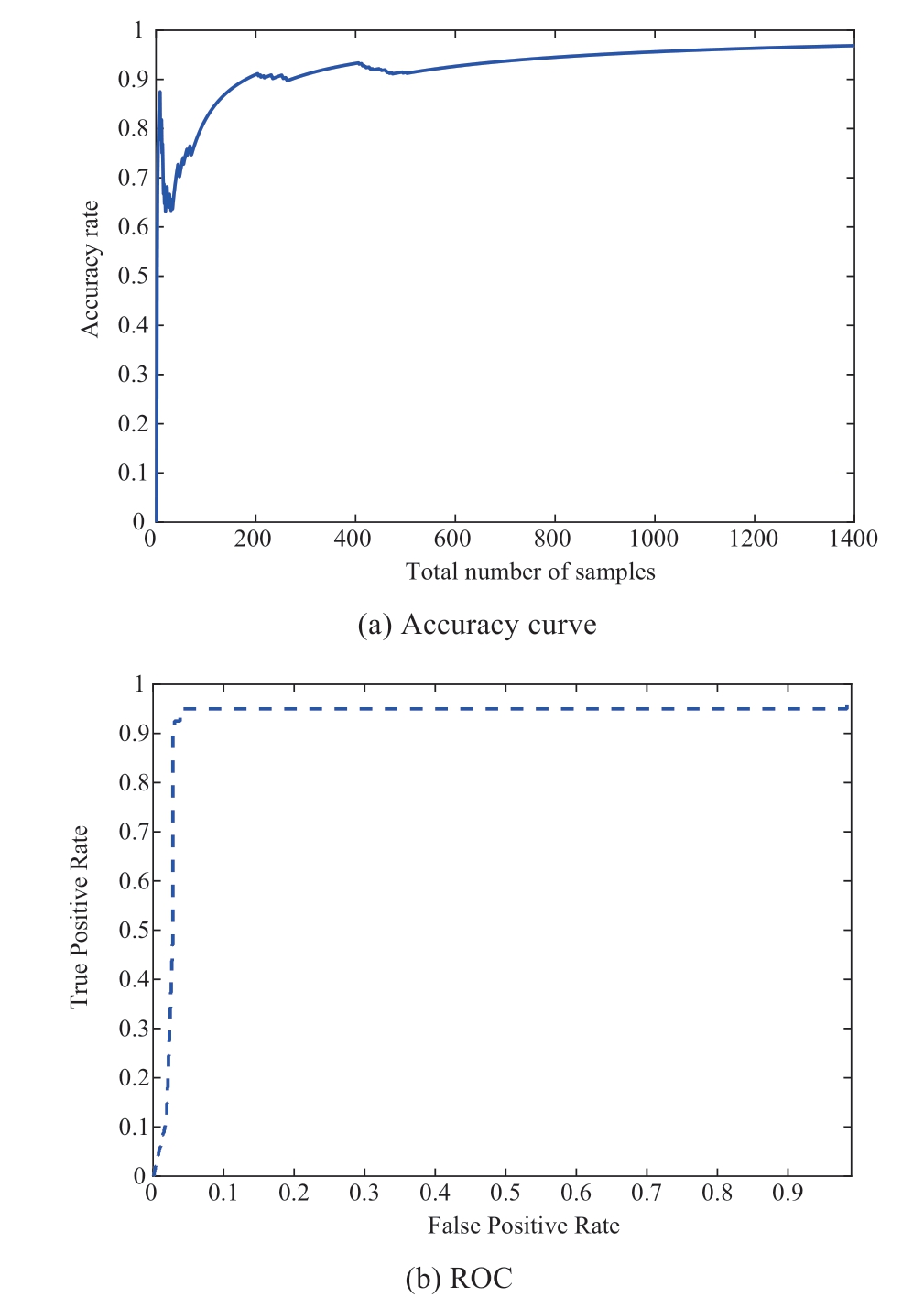
Fig.9 Prediction performance of DLAAs under dual RBF network model
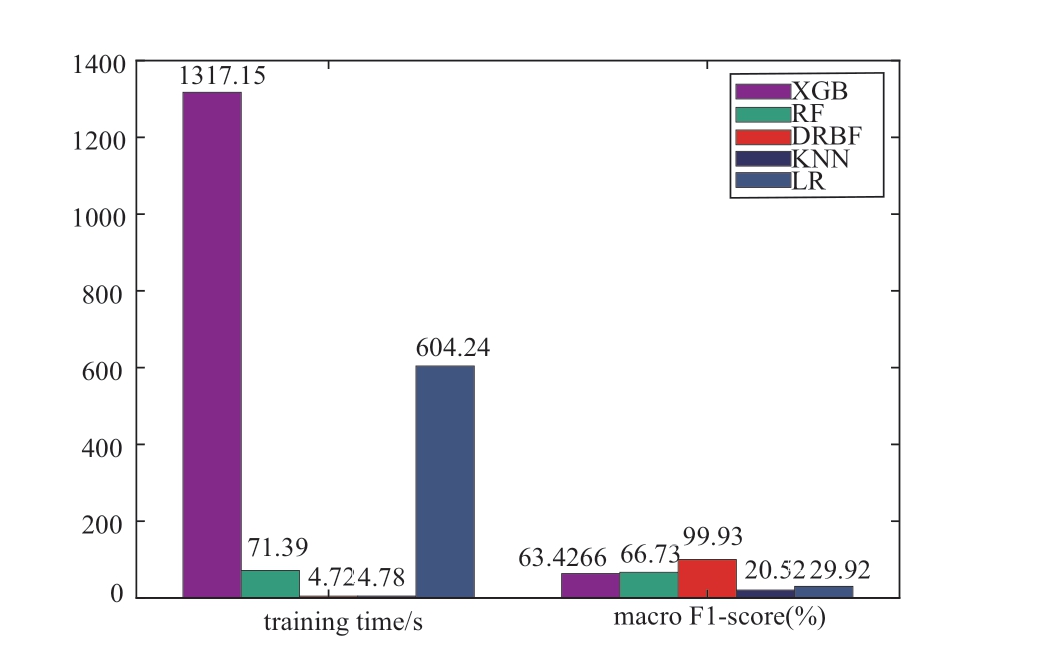
Fig.10 Performance comparison of attack prediction under different prediction algorithms
Thus, the proposed Algorithm 1 can quickly and accurately predict attack sequences in the cyber layer.Based on the above results, Algorithm 2 was applied to detect and locate the injected DLAAs.A bank of unknown input observers can be designed according to Algorithm 2.The corresponding simulation results for the area detection can then be obtained, as shown in Fig.11.
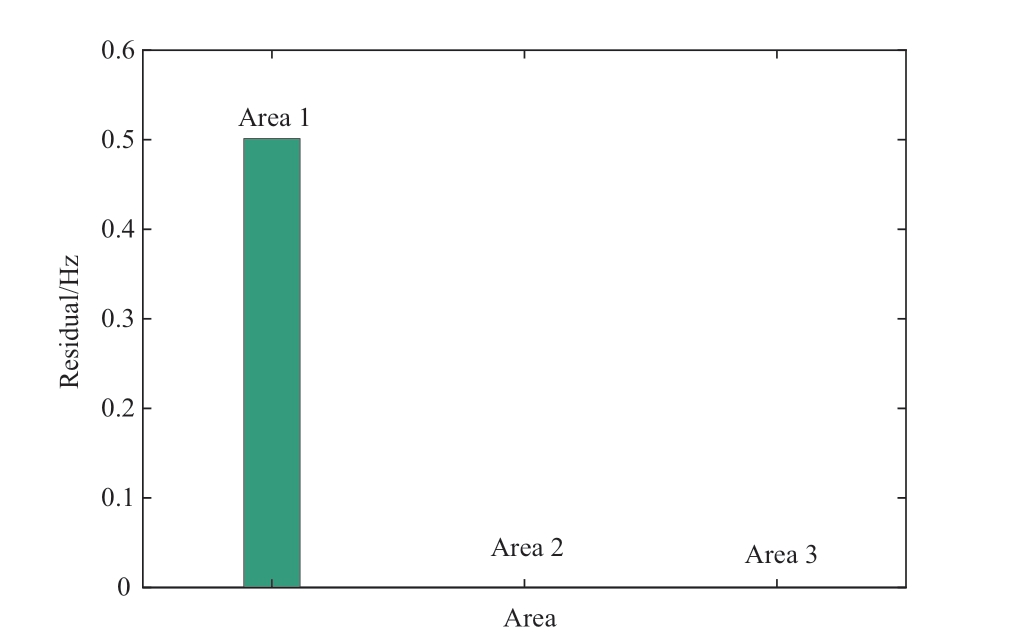
Fig.11 Area detection of DLAA on IEEE 14-bus grid system
A state residual was observed in the first grid area, as shown in Fig.11.The injected DLAAs can be effectively detected using Algorithm 2.To further locate the injected DLAAs, a bank of unknown input observers was designed for the attacked grid areas.Figures 12 and 13 show the changes in the running state and residuals under the DLAAs,respectively.
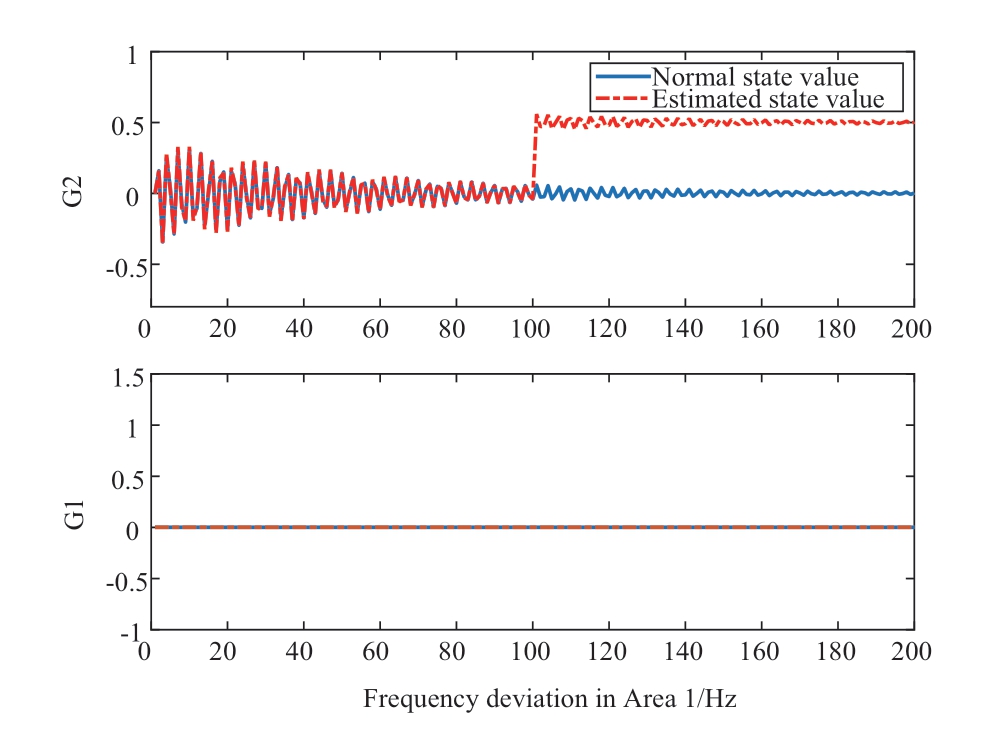
Fig.12 Change of running state in the 1st grid area on the IEEE 14-bus grid system
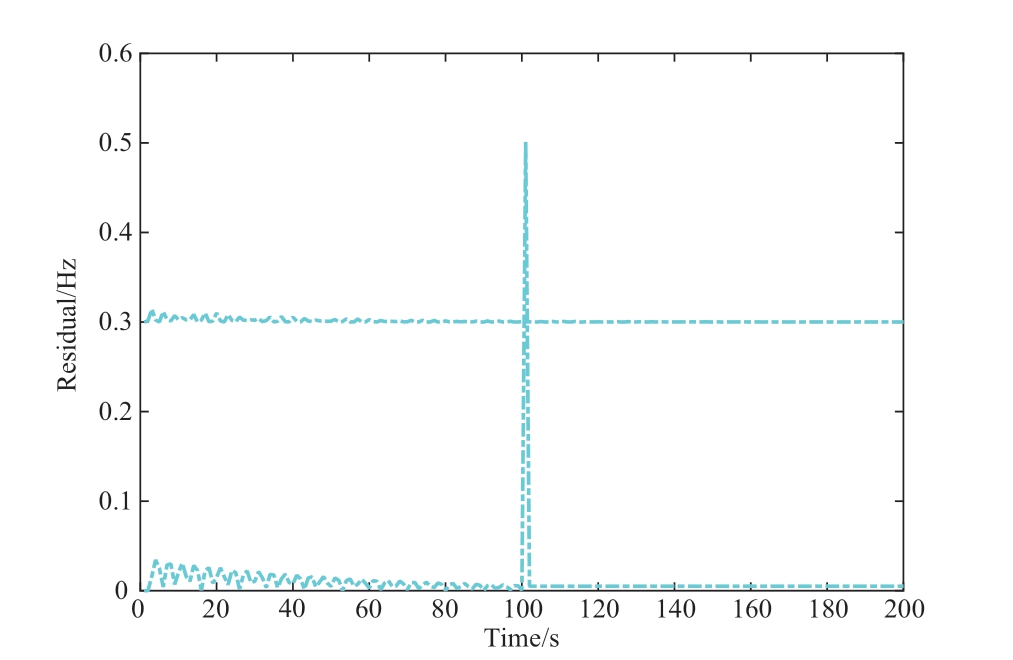
Fig.13 Change of state residuals on the IEEE 14-bus grid system
It is clear that the frequency deviation of the 2nd generator fluctuated at t = 100.6 s.The simulation results in Fig.12 indicate that the running state of the 2nd generator was affected by the injected DLAAs.Furthermore, the state residual of the 2nd generator exceeded the adaptive threshold, as shown in Fig.13.Using the proposed node logic decision in Algorithm 2, the injected DLAAs were located in the 2nd generator.In summary, the above simulation results demonstrated the effectiveness of the proposed cyber-physical collaborative detection and localization framework for DLAAs.
To evaluate the adaptive threshold-based detection performance against the DLAAs, the detection rate Pr was selected as follows [27]:

Based on the above detection performance, we obtain the detection rate and false alarm rate at different thresholds.Compared with the precomputed threshold-based detection methods in [19], the proposed adaptive threshold-based detection method enhanced the detection rate and reduced the false-alarm rate, as shown in Fig.15.Figure 16 shows the detection rates of the different detection methods.Compared with the results in [28] and [29], the proposed adaptive threshold-based detection method improved the detection performance.As the attack intensity increased,the developed detection method exhibited a better detection performance against DLAAs.
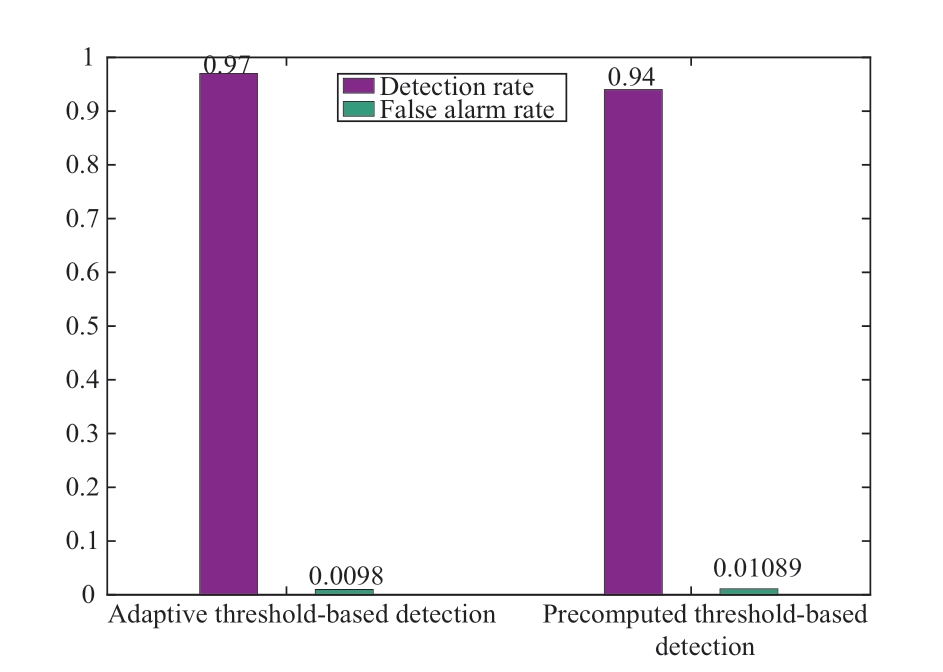
Fig.14 Detection performance under different detection thresholds
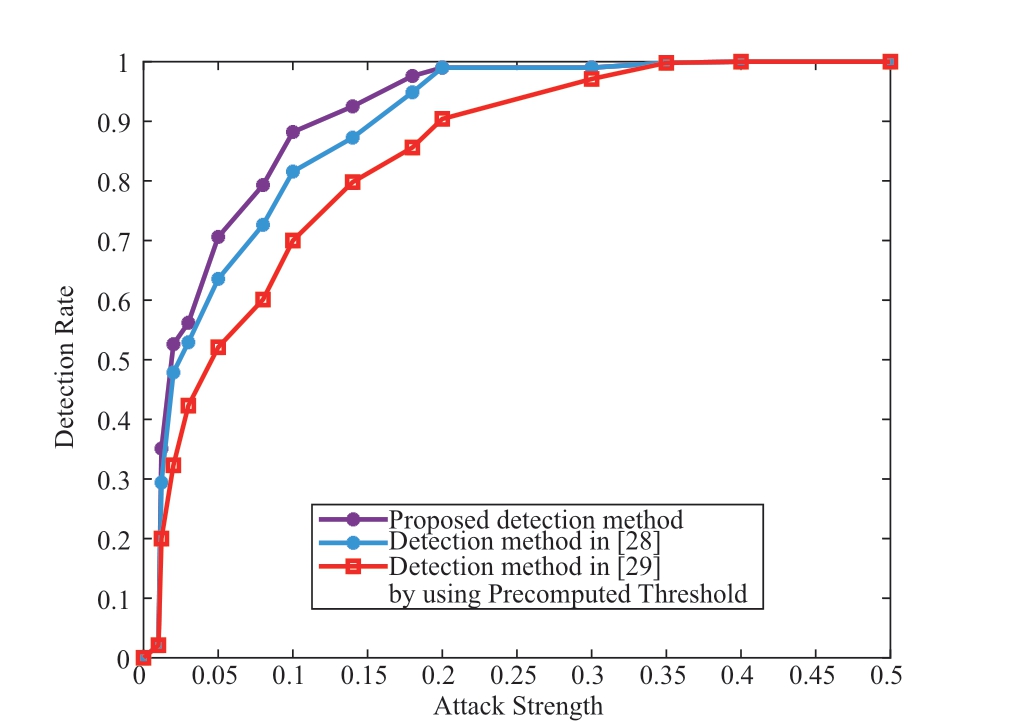
Fig.15 Detection rate of different detection methods
3.2 Case 2: collaborative detection and localization of multiple DLAAs on IEEE 118-bus grid system
Case 2 considers the detection and localization of multiple DLAAs in an IEEE 118-bus grid system.It was assumed that three DLAAs were injected by attackers in the IEEE 118-bus grid system.Specifically, the 1st DLAA, 2nd DLAA and 3rd DLAA were injected into the 2nd generator of the 1st grid area, 8th generator, and 12th generator of the 2nd grid area at t = 50, 100, and 120 s, respectively.Using the proposed dual-network model-based attack-prediction Algorithm 1, the attack-prediction result were obtained, as shown in Fig.16.
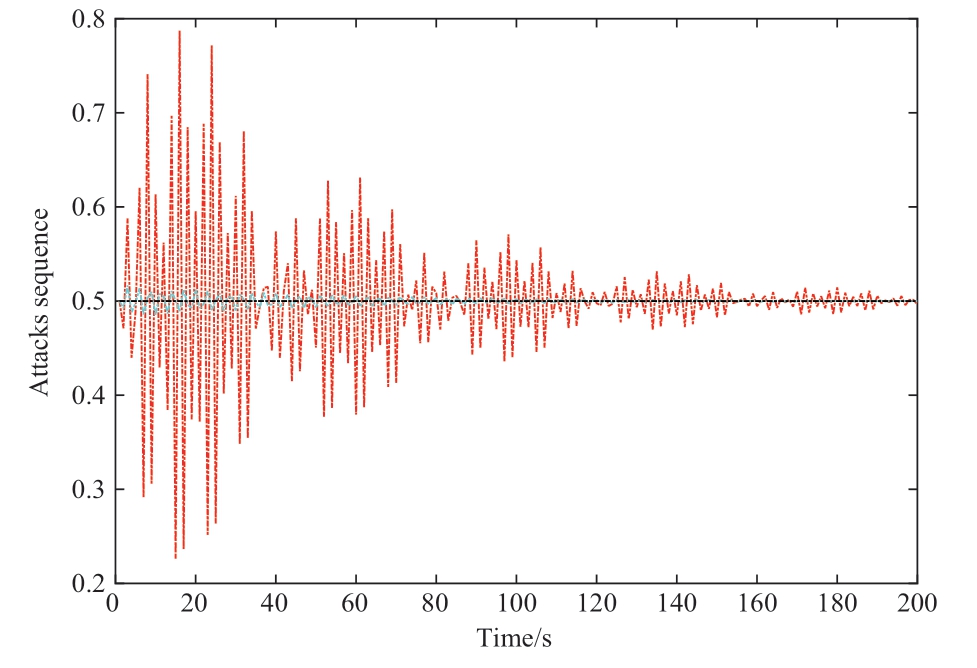
Fig.16 Prediction result of attack sequence on IEEE 118-bus grid system
As shown in Fig.17, an injected attack sequence exists in the cyber layer.However, the injected DLAAs were not detected or located.Therefore, the proposed unknown inputobserver-based detection and localization Algorithm 2 was further applied.A bank of unknown input observers was designed based on the constructed physical dynamic grid model.Figure 18 shows the change in the state residuals under the DLAAs for the five grid areas.
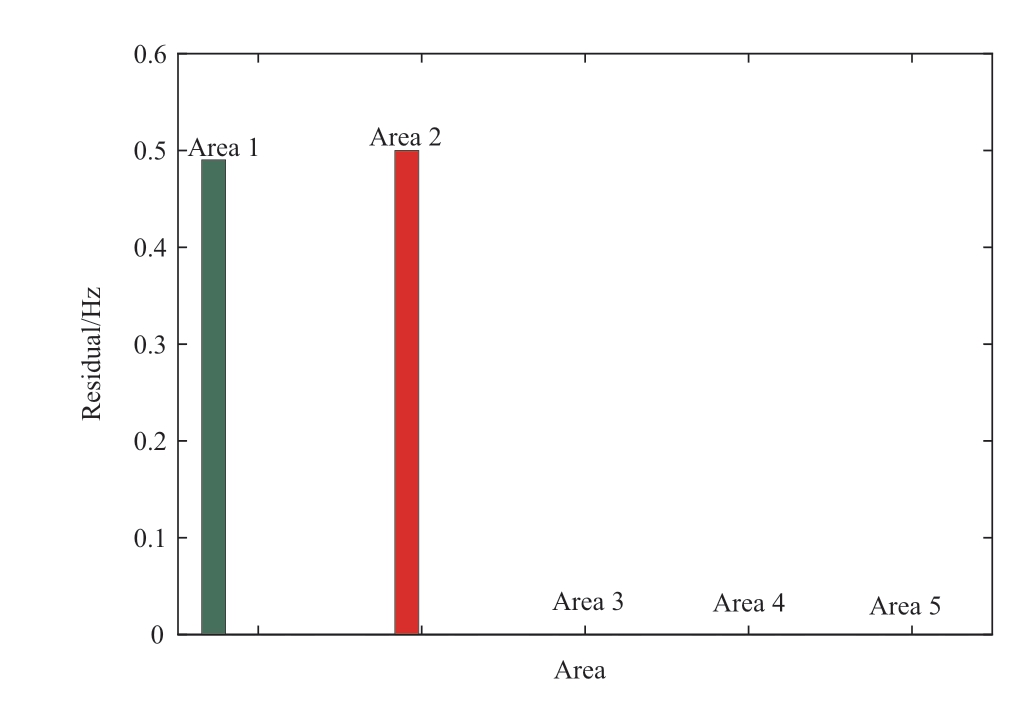
Fig.17 Area Detection of DLAA on IEEE 118-bus grid system
The simulation results in Fig.17 indicate that DLAAs exist in the 1st and 2nd grid areas.Therefore, the bank of the proposed unknown input observers must be located at the injected generator node.As shown in Figs.19 and 20, the changes in the running state and residuals under the DLAAs could be observed.
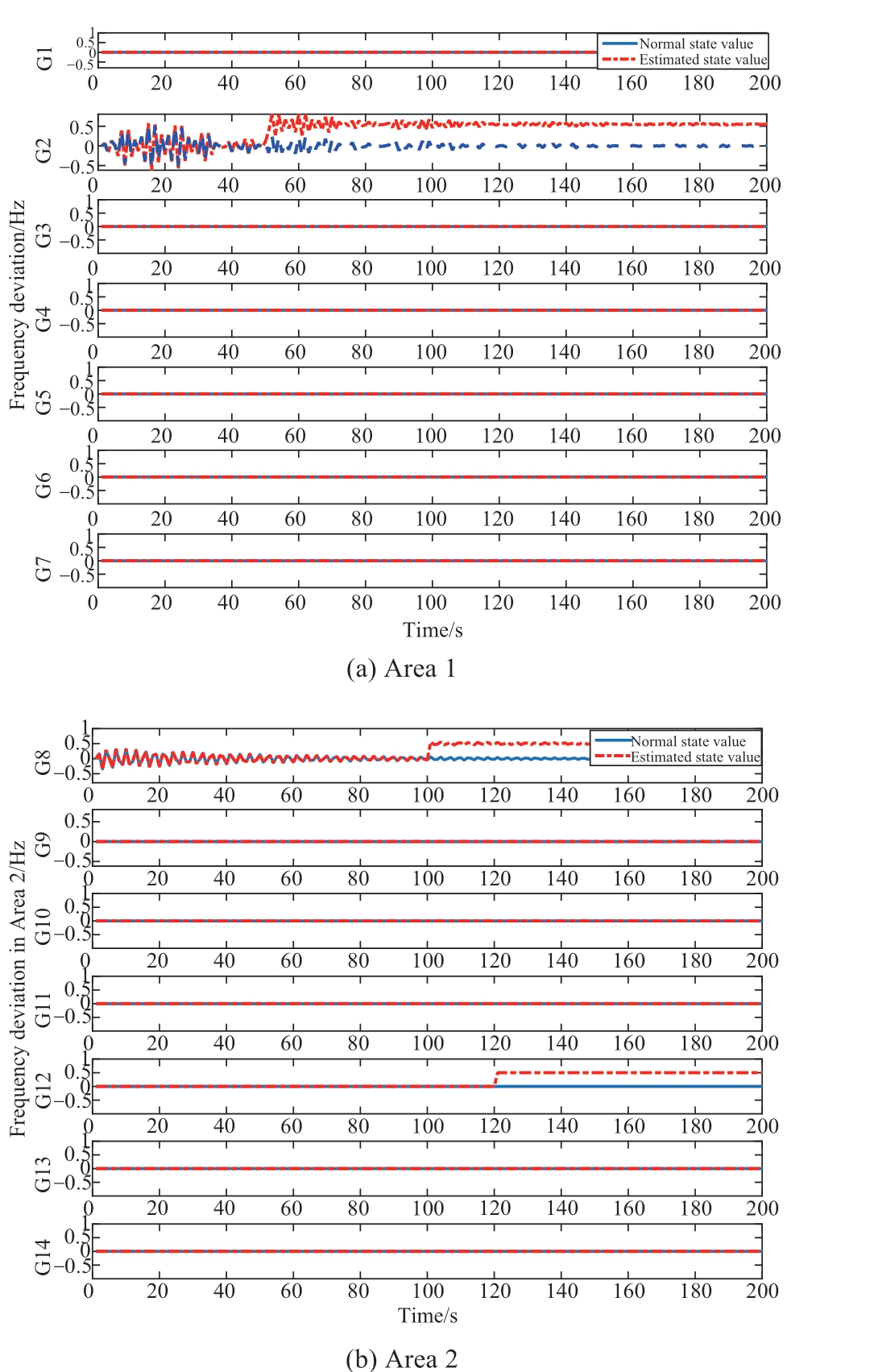
Fig.18 Change of running state on the IEEE 118-bus grid system
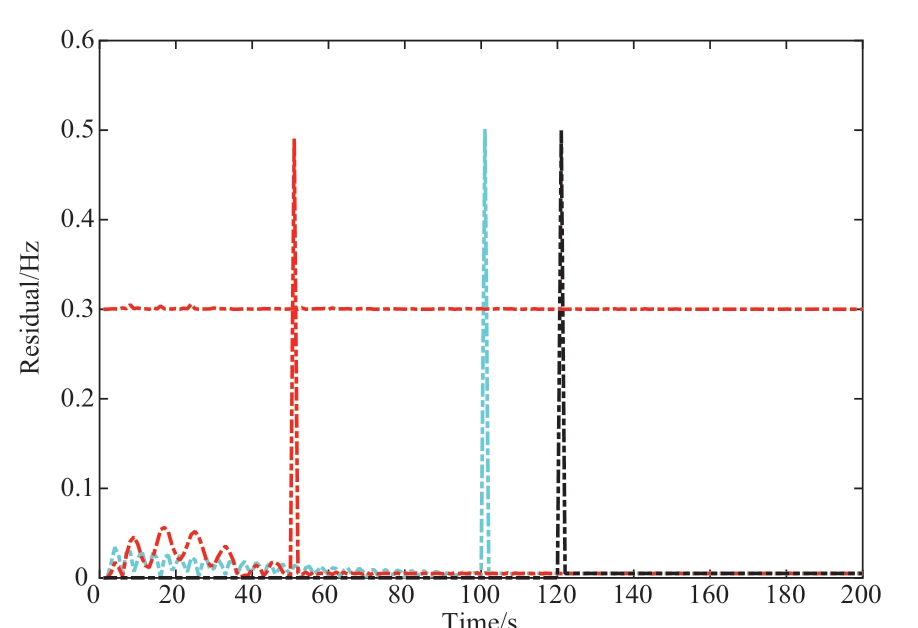
Fig.19 Change of state residuals on the IEEE 118-bus grid system
As evident, the frequency deviation fluctuated in case of the 2nd generator at t = 50.6 s, the 8th generator at t =100.5 s, and the 12th generator at t = 120.6 s.In response,the state residuals of the 2nd, 8th, and 12th generators all exceeded the designed adaptive threshold, as shown in Fig.19.Simultaneously, there were no fluctuations in the other generator buses.Using Algorithm 2, the multiple injected DLAAs were detected and located in the 2nd, 8th, and 12th generator nodes.In summary, the simulation results for the above cases demonstrated that the proposed cyber-physical collaborative scheme could detect and locate the injected DLAAs quickly.
4 Conclusions and discussion
In this study, we developed a novel cyber-physical collaborative detection and localization scheme for DLAAs in smart energy grids.The proposed method bridged the gap between style="font-size: 1em; text-align: justify; text-indent: 2em; line-height: 1.8em; margin: 0.5em 0em;">· A dual-RBF network-based prediction method was developed to improve the prediction performance of the DLAAs.
· An unknown input observer-based detection and localization method for DLAAs was proposed, and an adaptive detection threshold was designed to enhance the detection performance.
Future studies must focus on the following aspects.
· We must consider improvements to the attack prediction network, including the model parameters,structure, and dataset.
· Detection of multiple mixed attacks, such as denial of service attacks, false data injection attacks, and DLAAs must be investigated.
· The optimization and control of new energy systems under attack must be studied.
Acknowledgments
This work was supported by the National Nature Science Foundation of China under 62203376, the Science and Technology Plan of Hebei Education Department under QN2021139, the Nature Science Foundation of Hebei Province under F2021203043, and the Open Research Fund of Jiangsu Collaborative Innovation Center for Smart Distribution Network, Nanjing Institute of Technology under No.XTCX202203.
Declaration of Competing Interests
The authors have no conflicts of interest to declare.
References
[1]O Babayomi, Zhang ZB, T Dragicevic, et al.(2023) Smart grid evolution: Predictive control of distributed energy resources—A review, International Journal of Electrical Power and Energy Systems, 147: 108812
[2]Yu XH, Xue YS (2016) Smart grids: A cyber-physical systems perspective.Proc IEEE, 104: 1058-1070
[3]E Sisinni, A Saifullah, S Han, et al.(2018) Industrial internet of things: challenges, opportunities, and directions.IEEE Transacrions on Industrial Informatics, 14 (11): 4724-4734
[4]M M Raut, R R Sable, S R Toraskar (2016) Internet of things(IoT) based smart grid.international journal of engineering trends and technology, 34 (1): 15-20
[5]M D Smith, M E Paté-Cornell (2018) Cyber Risk Analysis for a Smart Grid: How Smart is Smart Enough? A Multiarmed Bandit Approach to Cyber Security Investment.IEEE Transactions on Engineering Management, 65(3): 434-447
[6]Protection CA(2016) Followup on western area power administration’s critical asset protection
[7]Attacks on the electricity grid US vulnerable to physical and cyberthreats n.d.https://www.cnbc.com/2014/01/03/ attacks-onthe-electricity-grid-usvulnerableto-physical-and-cyberthreats.html
[8]Liu Y, Ning P, Reiter M K (2011) False data injection attacks against state estimation in electric power grids.ACM Transactions on Information and System Security, 14(1): 1-33
[9]S Amini, F Pasqualetti, H Mohsenian-Rad (2018) Dynamic Load Altering Attacks Against Power System Stability: Attack Models and Protection Schemes.IEEE Transactions on Smart Grid, 9(4):2862-2872
[10]Wang HZ, Wen XC, Huang S, et al.(2021) Generalized attack separation scheme in cyber physical smart grid based on robust interval state estimation.International Journal of Electrical Power &Energy Systems, 129
[11]Ahmed S Musleh, Chen G, Zhao YD, et al.(2023) Spatiotemporal name="ref12" style="font-size: 1em; text-align: justify; text-indent: 2em; line-height: 1.8em; margin: 0.5em 0em;">[12]M Ganjkhani, S N Fallah, S Badakhshan, et al.(2019) A Novel Detection Algorithm to Identify False Data Injection Attacks on Power System State Estimation.Energies, 12(11): 1-19
[13]Xiong XP, Hu SD, Sun D, et al.(2022) Detection of false data injection attack in power information physical system based on SVM-GAB algorithm, Energy Reports, 8(5): 1156-1164
[14]Y Raghuvamsi, K Teeparthi (2023) Detection and reconstruction of measurements against false data injection and DoS attacks in distribution system state estimation: a deep learning approach.Measurement, 210: 112565
[15]Ma Q, Xu Z, Wang WT, et al.(2021) Dynamic load-altering attack detection based on adaptive fading Kalman filter in power systems.Global Energy Interconnection, 4(2): 184-192
[16]Su QY, Li SQ, Gao YC, et al.(2021) Observer-based detection and reconstruction of dynamic load altering attack in smart grid.Journal of the Franklin Institute, 2021(02): 008
[17]Wang XY, Luo XY, Pan XY, et al.(2020) Detection and Location of Bias Load Injection Attack in Smart Grid via Robust Adaptive Observer.IEEE Systems Journal, 14(3): 4454-4465
[18]M Adeli, M Hajatipour, M J Yazdanpanah, et al.(2022)Optimized cyber-attack detection method of power systems using sliding mode observer.Electric Power Systems Research, 205:107745
[19]Wang XY, Luo XY, Zhang MY, et al.(2019) Detection and isolation of false data injection attacks in smart grids via nonlinear interval observer.IEEE Internet Things, 6(4): 6498-6512
[20]V Katewa, F Pasqualetti (2021) Optimal Dynamic Load-Altering Attacks Against Power Systems.2021 American Control Conference (ACC), 4568-4573
[21]J Opitz, S Burst (2019) Macro f1 and macro f1.arXiv preprint.arXiv: 1911.03347
[22]Dehghani M, Nikravesh S (2008) State-space model parameter identification in large-scale power systems.IEEE Trans Power Syst, 23(3): 1449-57
[23]T Iwasake, S Hara (2005) Generalized KYP lemma:Unified frequency domain inequalities with design applications.IEEE Transactions on Automatic Control, 50(1): 41-59
[24]Wang H, Yang GH (2008) A finite frequency domain approach to fault detection observer design for linear continuous-time systems.Asian Journal of Control, 10(5): 1-10
[25]J H Chow, G Peponides, P V Kokotovic, et al.(1982) Time-Scale Modeling of Dynamic Networks with Applications to Power Systems.New York, NY, USA: Springer-Verlag
[26]Ding SX (2008) Model-based fault diagnosis techniques.Springer, Berlin, Heidelberg
[27]Marwa Houiji, Rim Hamdaoui, Mohamed Aoun (2016) Fault detection performances analysis for stochastic systems based on adaptive threshold.the 13th International Multi-Conference on Systems, 617-624
[28]Luo XY, Zhu MG, Wang XY, et al.(2022) Detection and isolation of false data injection attack via adaptive Kalman filter bank
[29]J Nagi, K S Yap, S K Tiong, et al.(2011) Improving SVMbased nontechnical loss detection in power utility using the fuzzy inference system.IEEE Transactions on Power Delivery, 26(2):1284-1285

Scan for more details
Received: 21 May 2023/Revised: 6 September 2023/Accepted: 11 October 2023/Published: 25 June 2024
Xiaoyuan Luo
xyluo@ysu.edu.cn
Xinyu Wang
wxyzmya@ysu.edu.cn
Xiangjie Wang
xjss@stumail.ysu.edu.cn
Xinping Guan
xpguan@ysu.edu.cn
Shuzheng Wang
wsz310@126.com
2096-5117/© 2024 Global Energy Interconnection Group Co.Ltd.Production and hosting by Elsevier B.V.on behalf of KeAi Communications Co., Ltd.This is an open access article under the CC BY-NC-ND license (http: //creativecommons.org/licenses/by-nc-nd/4.0/ ).
Biographies

Xinyu Wang received his Ph.D.degree from the Institute of Electrical Engineering, Yanshan University, Qinhuangdao, China, in 2020,respectively.His research interests include fault detection and fault tolerant control, and multiagent and networked control systems.

Xiangjie Wang is currently pursuing her degree of M.Eng in electrical engineering at Yanshan University, Qinhuangdao.Her research interests cover in detection, isolation,and defense of cyberattack of CPS.

Xiaoyuan Luo received his M.Eng.and Ph.D.degrees from the Institute of Electrical Engineering, Yanshan University,Qinhuangdao, China, in 2001 and 2004,respectively.His research interests include fault detection and fault tolerant control, and multiagent and networked control systems.

Xinping Guan received his M.Eng.and Ph.D.degrees from the Harbin Institute of Technology, Harbin, China, in 1991 and 1999,respectively.He is currently a Chair Professor with Shanghai Jiao Tong University, Shanghai,China.He is a National Outstanding Youth Honored by NSF of China, Changjiang Scholar by the Ministry of Education of China and State-level Scholar of New Century Bai Qianwan Talent Program of China.As a principal investigator, he has finished/been working on many national key projects.

Shuzheng Wang received his Ph.D.degree from the Electrical Engineering, Southeast University, China, in 2020.He is mainly engaged in research on new energy generation and grid connection technology for new power systems.
(Editor Yanbo Wang)
